Networking Field Day 25, Part 1
I was invited to be a delegate at Networking Field Day 25 and it did not disappoint in the slightest. It was by far one of the best community event experiences I’ve had in networking so far. It’s hard to believe that I really only started this networking-focused journey 5 or less years ago, and I get to sit in the same virtual room as some very well-respected minds in Networking. In addition to getting to meet the other delegates, we were graced with an extremely busy schedule of presentations from the following vendors: Kemp Technologies, VMware, Arrcus, Intel, Path Solutions, Nokia, Aruba Networks, Juniper Networks, and IP Infusion.
This NFD25 was so jam-packed with presentations that I need to split up this initial post into Part 1 and Part 2 to cover all of the content. The presentations I will cover in this Part 1 are from the following vendors: Kemp, VMware, Arrcus, Intel, PathSolutions
To check out the recorded presentations, take a look at the event page here
This is my initial post where I want to capture my over-arching thoughts on Networking Field Day 25 and the vendor presentations. In later posts, I want to dive into specific vendors and technologies that were brought to the table at NFD25.
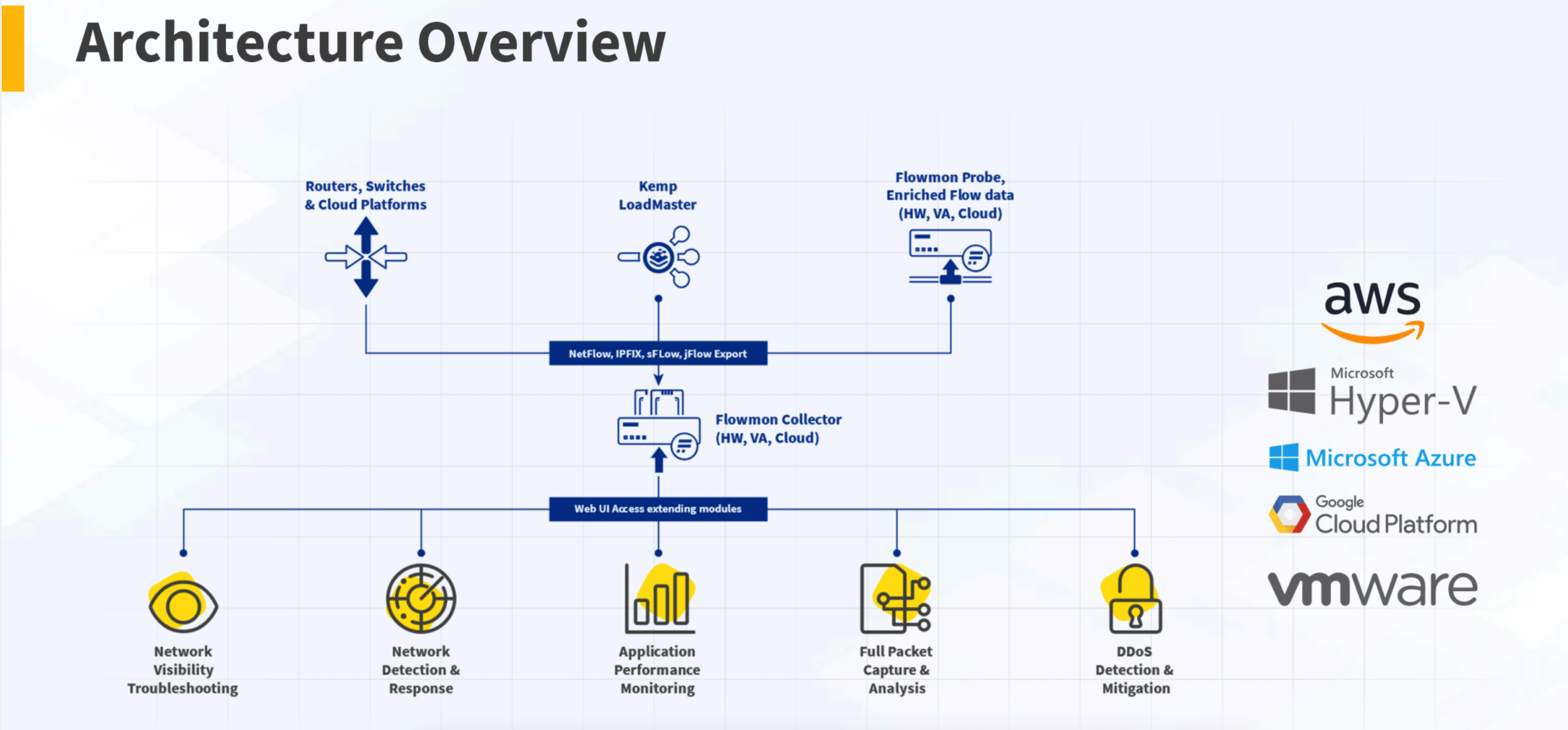
For Kemp Technologies, the focus was on the integration of the Flowmon product, which they acquired in 2020, and how it fit into the Kemp portfolio of always-on Application Experience metrics. The architecture Kemp presented features flowmon probes that collect network flow information in your on-prem or cloud environments from a span or tap. From there data can be fed into the Flowmon collector where Kemp strives to allow for a number of functions including Application Performance Monitoring, DDoS Detection/Mitigation, and others.
One cool difference right off the bat is that instead of just exporting flow data directly off of your hardware boxes, you are dumping data straight to the flowmon probes via span/tap so there is more opportunity for granular data collection at the probe level. For those who may be less familiar with the format of flows, you get metadata on several things including TCP/UDP ports for a connection, source and destination IP address, source and destination MAC address, BGPNextHop, SrcAS and DstAS potentially, flow direction, TCP flags, Vlan ID, and other valuable tidbits of information sent from network gear. But what don’t you get with that vanilla flow exporting from boxes that you could get with the flowmon probe and collectors? The full packet content including Application-level headers.
Why does Kemp say this data is useful?
Mainly, in their presentation Kemp pointed out their ability to recognize patterns within packet data sets that you wouldn’t normally see in regular flow data. However, you can make a completely valid argument that with encryption taken into consideration there will be many, many false-positives when using this data for security analytics and detection. Even with all of the available packet data, without visibility into the application or system hosting the application with certain level of intelligence - it’s extremely difficult for a flow analyzer to make an intelligent call on what’s an attack on a service vs. what is Bob pressing enter with a wrong password many times.
I think that if the Kemp system was able to take it just a little further, coupled with some application-aware intelligence this would be a very strong solution for both proving “it’s not the network” as well as defending against real security attacks. The network data is helpful to someone focusing on networking and that knows networking, but those often are not the same people working on the security team or having issues troubleshooting an application’s performance.
Catch the Kemp NFD25 presentation here
vRNI
VMware introduced us to vRNI (VMware vRealize Network Insight) whose goal is to monitor the modern networks of today. I’m sure you are no stranger to the idea of “actionable insights” at this point, and it has become more and more common in software-defined conversations over the last few years. With companies having many workflows in the cloud, network teams quite frankly need “eyes in the sky” to isolate issues and plan for remediation.
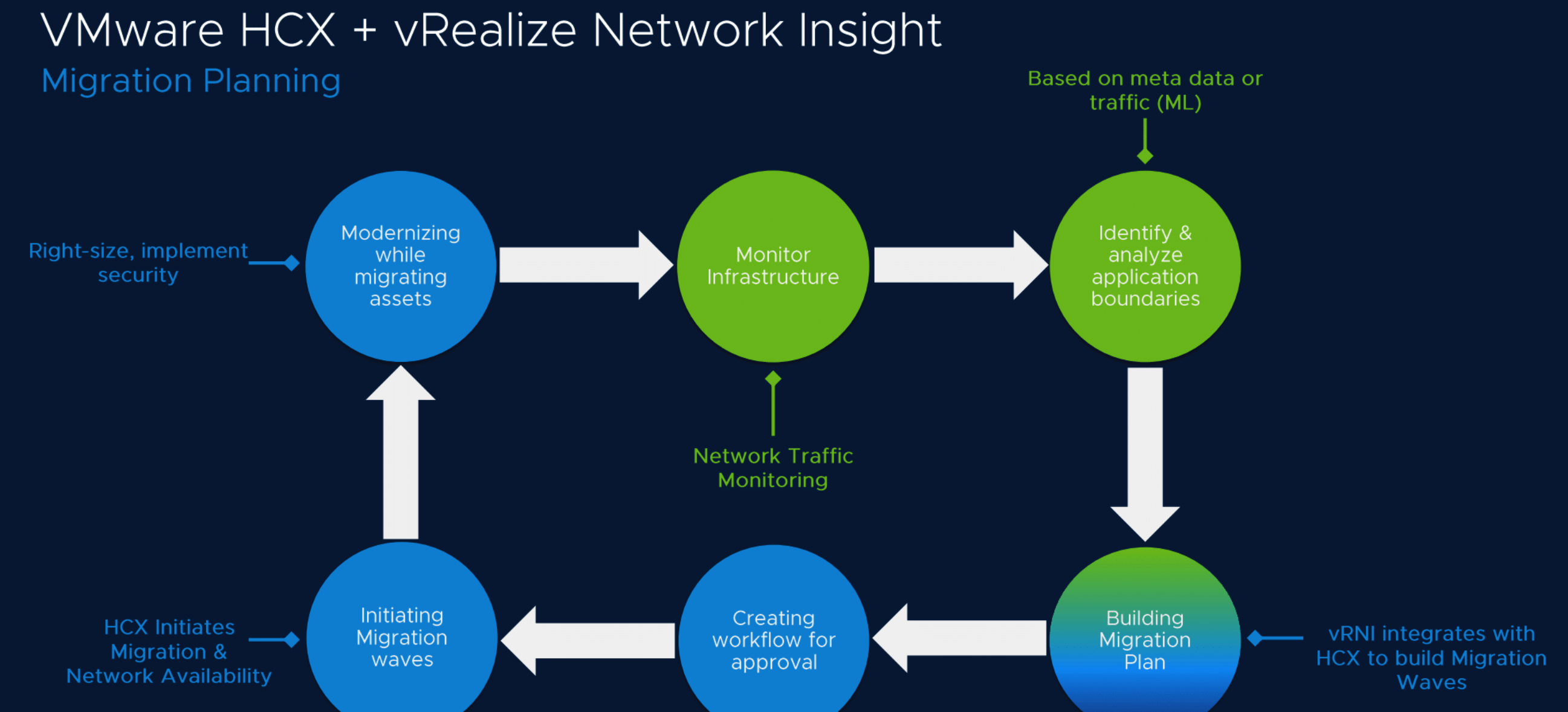
One use-case that VMware showed for vRNI was in a migration from on-prem to cloud. vRNI could be used to discover applications in a local environment, and VMware HCX could be used to create an L2 extension (yuck) between on-prem and cloud networks. The HCX L2 extension would be used to migrate VMs from on-prem hypervisors to the specific cloud environment of choice. In the demo the VMware team shared with us, they mainly used flows as the source of application discovery and if you think about it that is a convenient way for a network engineer to discover the application playground.
Network Assurance and Verification
For me, this was a very cool part of the VMware presentation, and that’s not just because the presenter’s name was similar to mine (Brighten). In 2019, VMware acquired Veriflow and Brighten joined the VMware team as a part of that acquisition. With Veriflow came experience in intent verification and troubleshooting for resilient customer networks. The idea is that vRNI can consume flows of “what is happening” and state from devices to see “what can happen”, as well as Intents modeled from the customer. This, as well as the application insights from the flows discovered earlier, can allow vRNI to make intelligent decisions about what is an anomaly, what intents are not being met within the network, and what isn’t able to be verified.
In the demo, VMware shows us an example network with anomalies based off of defined intents and network state/flows. The coolest part of this piece was it’s not only usable for VMware devices, but also other vendors. For network switches and routers in the underlay, state and flows can be pulled to assure the underlying network devices. Because even though we are doing all this overlay networking in modern day, there’s still 1’s and 0’s down there somewhere to contend with.
For all the VMware presentation goodness, you can go and check it out
I did some preliminary work leading up to the presentation by Arrcus. I checked out their website and read a little bit about their vRR and their VDR (distributed chassis technology). I can’t help but read about distributed chassis systems that are managed by a centralized controller and start to think about all-or-nothing software upgrades. Good new however, I asked Arrcus how they handle software upgrades in their VDR and they reported they have graceful control plane upgrades while maintaining forwarding state. I’ve had a wishy-washy history with these sort of things, but their answer leaves one hopeful.
SRv6 Demo
As far as the presentation went, I really enjoyed the demo by Arrcus showing off some L3VPN (v4/v6) over SRv6 transport. I really urge you to watch that video segment and pay close attention to Matt Anderson when he explains the roles of the different SIDs. I really compliment Matt on his demo in highlighting the TABLE ID values and forwarding actions when packet is received. For me, this was all very easy to follow even after being an extreme MPLS nerd.
For me, Arrcus seems to have a very flexible operating system on their hands. They also support standard API’s and, as shown with the SRv6 demo, they are embracing modern transport technologies and overlays. I think the only thing missing from Arrcus is a all-in-one solution featuring a Network Management and Orchestration platform. They have Arrcus Insights in the form of ArcIQ which provide visibility into the underlay and overlay control plane protocols, but they lack the vendor-provided orchestration system for the fabrics and routing topologies. Overall I really enjoyed hearing about Arrcus and it was my first introduction to the company, and their demo featuring SRv6 definitely stuck my interest.
Ed Horley has already written a fantastic post on the Intel presentation about Silicon Photonics at NFD25. For me, optics have almost become something you take for granted. In the world of ISP networking, you stand up a new link over leased or owned dark fiber, you plug in an optic at the ends whether it be BiDi, DWDM, CWDM, duplex, etc and you’re off to the races after a few tests (Well, maybe more than a few). And, each time I run into a worthwhile optical presentation, I’m fascinated by all I don’t know.
With bandwidth consumption rising exponentially as we add more and more devices feeding off our networks, the optics are expected to keep up with the ever-growing need for more speed and low latency computing.
Growing, Growing, Growing
Like I said, I’m not an optical guy flourishing in the optical space. I know the basics, like 40G may as well be dead and 100G + 400G are where the money should be invested. I know enough to be dangerous, but then we entered unchartered territory for someone like me..
- What we are used to seeing - the laser, modular, and lenses are carefully aligned and placed
- The one she told you not to worry about - silicon photonics, discretely placed on silicon, a truly integrated design in a single piece
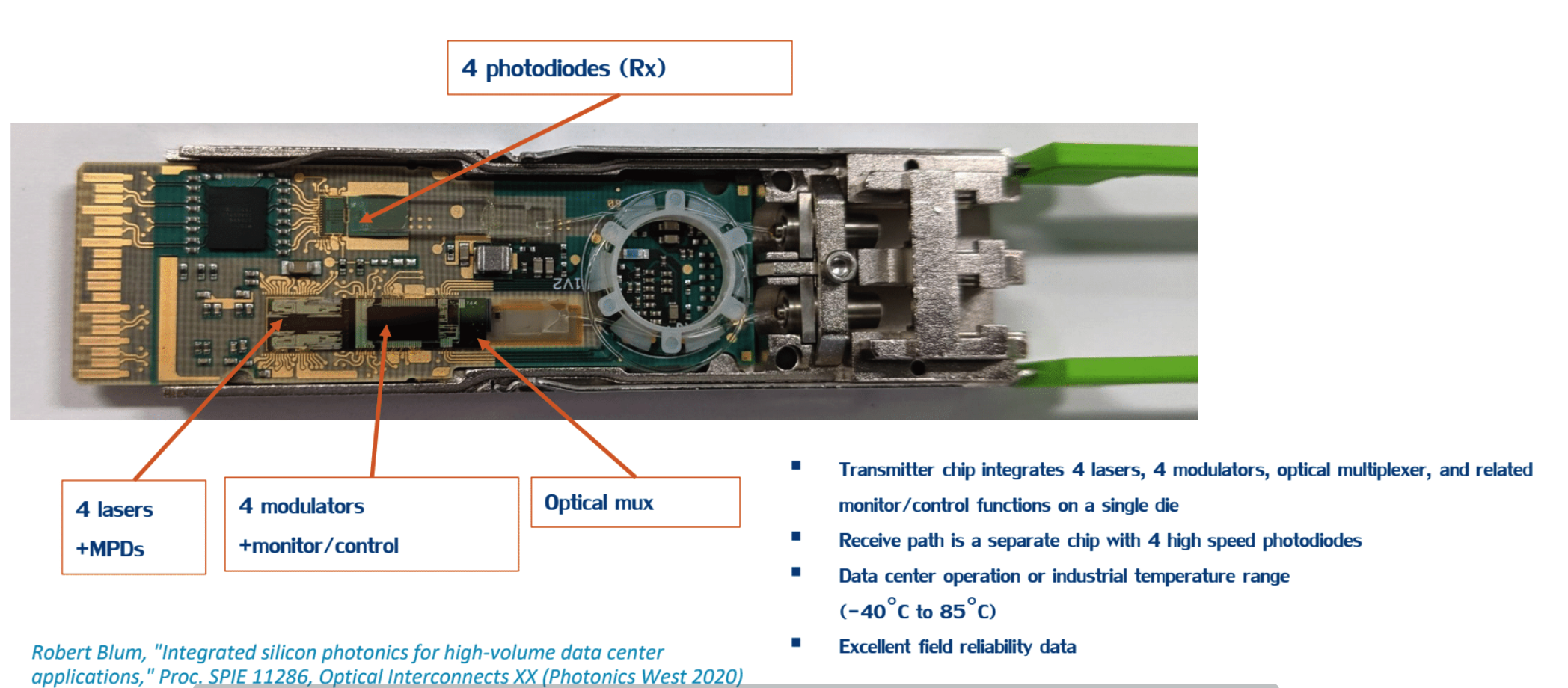
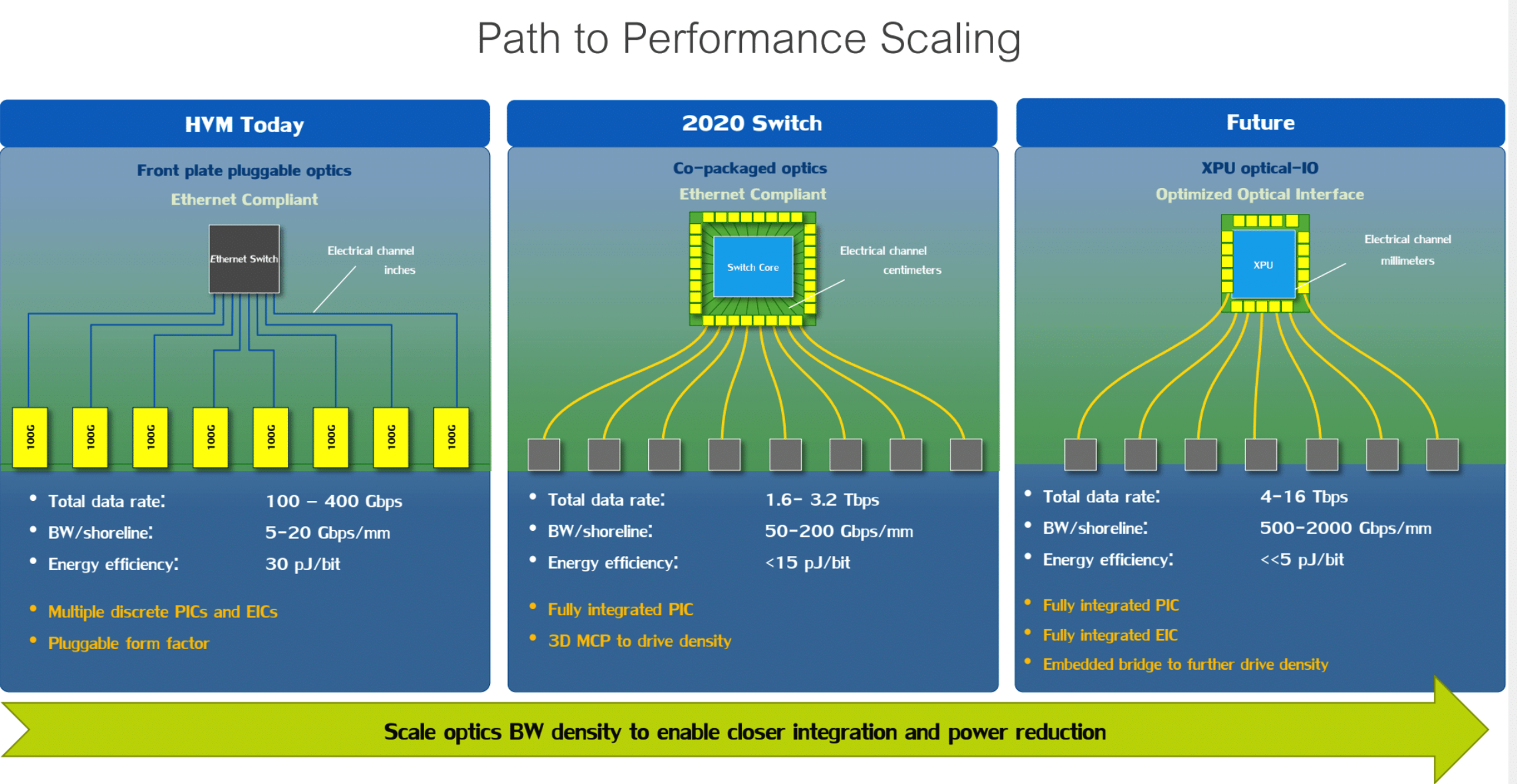
To say this was cool to see would be an understatement. If you didn’t catch this presentation, you really should go back and check it out. Intel also spoke about shortening the electrical channel between switch chip and interface port. By doing so, one can guarantee higher bandwidth with the most energy efficiency, lowering power consumption and heat.
Intel had a PoC switch leveraging co-packaged optics, bringing the optical further into the hardware, nearer the chip and shortening the electrical channel run. This could be the future of packet switching via optical, 400G and above.
I really enjoyed listening to Tim from PathSolutions discuss what they’ve done for their customers. Right away, he discussed their strengths and upbringing in helping customers troubleshoot voice calls. From there, it seems as though the company has grown into providing a TotalView of the network for operators. PathSolutions provides a rich toolset for the operators looking to take control of the user network experience.
For those larging large layer 2 domains (yuck) or small ones (good for you), you could find use out of the PathSolutions softwares. Easily searching for MAC address to port relationships, IP->MAC ARP mapping, and other troubleshooting information is put into the palm of your hands. As someone who has worked to support school campus networks, I know exactly how valuable this information can be to an operator. When you’re tracking down a fire, the last thing you want to do is jump through from the head-end router down to the acces switch just to find a single MAC address hanging off the edge port.
The PathSolutions product pulls a slough of information via SNMP and makes the best use of it. Tim also displayed the ability to capture netflow data from network gear, so potentially you have that at your disposal as well when working with PathSolutions. Personally I view the PathSolutions product as a shortcut to finding network-related fires and proving “it’s not the network.” Especially for small to midsize companies, I think that this product offering has a lot to say.
Check out PathSolutions here
Wrapping Up Part 1
Like I said in the intro, I will have Part 2 coming soon with the presentations by Nokia, Juniper Networks, IP Infusion, and Aruba Networks. I’m looking forward to putting more pen to paper about NFD25 and I can’t wait for the next Networking Field Day.
Disclosure
I was invited to be a delegate at NFD25, no gifts or swag influenced my decisions in writing this blog post. My participation in the event and in this content is all voluntary. Gestalt IT was nice enough to host the other delegates and myself virtually on the big screen of Networking Field Day 25. Some swag gifts were provided by the sponsors to us delegates, but I did not expect anything and there was no further requirement of delegates to participate in blog content. All thoughts are my own and straight from my keyboard to your viewing eyes.